Introduction
In the modern digital world, securing communication and data transmission is crucial. One of the most effective ways to achieve this is through Public Key Infrastructure (PKI), a framework that enables secure communication over insecure networks. PKI provides encryption, authentication, and digital signatures to protect data integrity and confidentiality.
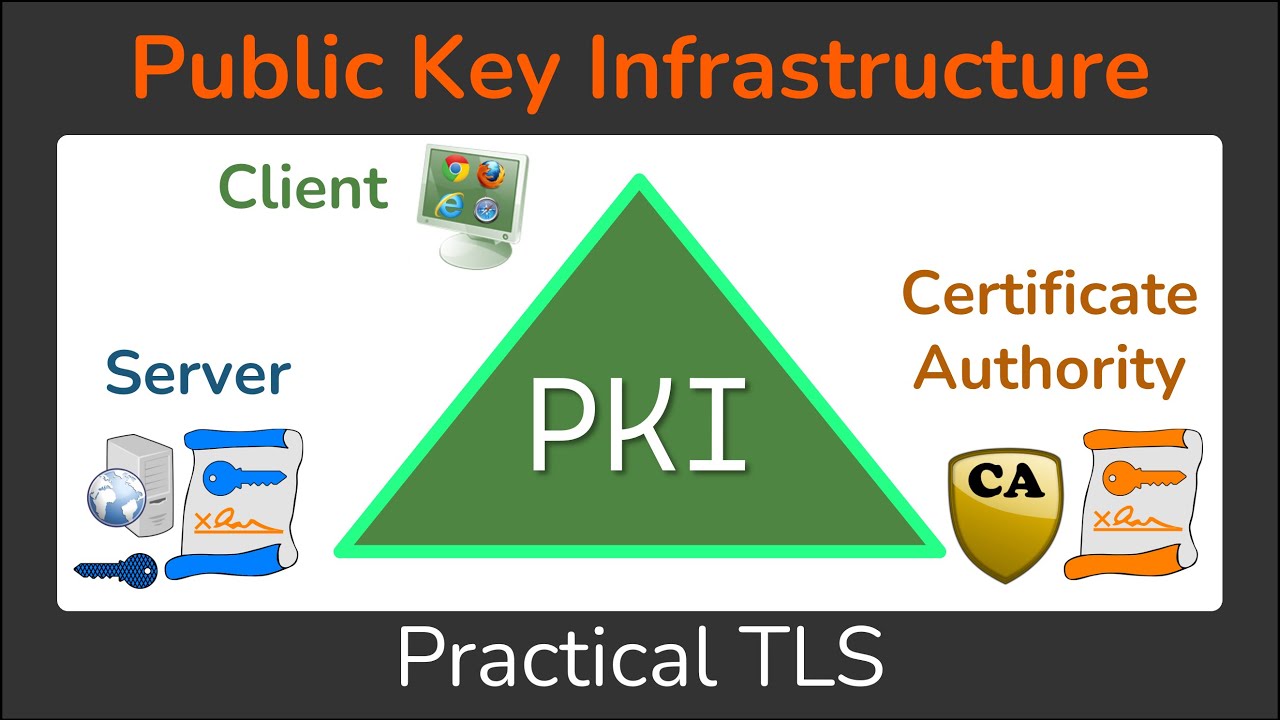
What is Public Key Infrastructure (PKI)?
PKI is a system of hardware, software, policies, and procedures that manage public-key encryption and digital certificates. It is primarily used to establish a trusted environment for electronic transactions by ensuring that entities are who they claim to be and that data remains secure.
Core Components of PKI
PKI consists of several key components that work together to provide secure digital communication:
-
Certificate Authority (CA) – The CA is responsible for issuing, verifying, and revoking digital certificates. It acts as a trusted third party in the PKI ecosystem.
-
Registration Authority (RA) – The RA acts as an intermediary between users and the CA, verifying user identities before a certificate is issued.
-
Digital Certificates – These are electronic credentials that associate a user's identity with a public key. Certificates follow standards like X.509 and help verify authenticity.
-
Public and Private Keys – PKI relies on asymmetric cryptography, where a user has a public key (shared) and a private key (kept secret). The private key is used for encryption and digital signatures, while the public key is used for verification.
-
Certificate Revocation List (CRL) – A list of revoked certificates that are no longer trusted. CAs publish these lists to ensure security.
-
Key Management Services – These services help in generating, storing, distributing, and revoking cryptographic keys securely.
How PKI Works
The PKI process follows a structured workflow to establish trust:
-
A user requests a digital certificate from the RA.
-
The RA verifies the user’s identity and forwards the request to the CA.
-
The CA issues a digital certificate, binding the user’s identity with a public key.
-
The certificate is distributed to the user and stored in a repository for public access.
-
When a user sends an encrypted message, the recipient uses the sender’s public key to verify its authenticity and decrypt it.
-
If a certificate is compromised, it is added to the CRL and no longer trusted.
Applications of PKI
PKI plays a crucial role in various industries and applications, including:
-
Secure Email Communication – Encrypts emails and ensures authenticity using digital signatures.
-
Website Security (SSL/TLS Certificates) – Enables HTTPS to secure website traffic and protect user data.
-
E-Government Services – Used for secure document signing and identity verification.
-
Financial Transactions – Ensures secure banking transactions and online payments.
-
Cloud Security – Protects cloud-based applications and data.
Benefits of PKI
-
Enhanced Security – Provides strong encryption and authentication mechanisms.
-
Data Integrity – Ensures that information is not altered during transmission.
-
Scalability – Can be implemented across large organizations and global networks.
-
Trust and Compliance – Meets regulatory requirements and builds user trust.
Challenges of PKI
Despite its benefits, PKI faces several challenges:
-
Complex Implementation – Requires careful planning, infrastructure, and management.
-
Certificate Management Overhead – Maintaining and renewing certificates can be resource-intensive.
-
Security Risks – If a private key is compromised, it can lead to unauthorized access.
Conclusion
Public Key Infrastructure (PKI) is a fundamental technology for securing digital communications. By leveraging encryption, authentication, and digital certificates, PKI helps protect sensitive data and prevent cyber threats. While it comes with challenges, its benefits make it an indispensable solution for organizations looking to enhance security in the digital age.
Comments on “Public Key Infrastructure (PKI): A Complete Guide”